JR Raphael, PC World - Less than 24 hours after Michael Jackson's death, fraudsters are exploiting public interest with their attempts to spread spam and malware. Security researchers say they've observed hundreds of cases of malicious messages masquerading as information about Jackson's death. Some of them, they say, popped up within minutes of the news.
Avoiding these threats isn't difficult, though: It's just a matter of staying one step ahead. Here are some of the attackers' tactics and what you can do to keep from falling victim.
E-Mail Address Harvesting
E-mails started circulating Thursday claiming to have "vital information" about Jackson's death. The messages ask users to respond in order to become privy to the "secret" details.
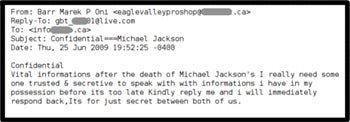
Unlike many Web-based threats, these e-mails aren't attempting to get you to click onto anything; rather, analysts believe, they're likely trying to get you to reply so your address can be confirmed for future spamming purposes.
"The spammer can easily harvest recipients' e-mail addresses via a free live e-mail address if computer users reply to the spam message," researchers at security firm Sophos explain.
Hidden Trojan Infecting
Another hoax takes the more standard approach of offering e-mail-based links, supposedly to exclusive videos and photos of Michael Jackson. These messages also appear to have YouTube videos embedded inside. If you try to follow the links or play the video, however, you may end up with malware on your computer -- without even knowing it.
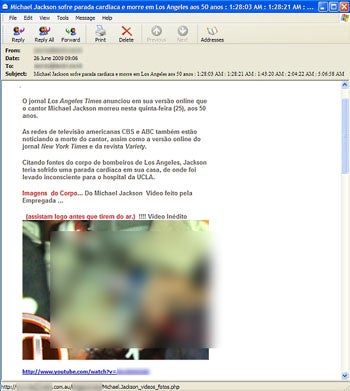
"A legitimate Web site ... is opened by the default browser in order to distract the user by presenting a news article for them to read," researchers at Websense Security Labs explain. "In the background, three further information-stealing components are downloaded and installed."
Background Blog Processing
Other attackers are getting more creative and setting up phony Michael Jackson-related blogs to try to trick unsuspecting users. Security company Webroot says it's seen such efforts pop on a variety of hosting services, including Google's Blogger platform. The blogs take advantage of background processing to run scripts that can cause serious harm to your system.
"Just visiting [one] page spawned a tornado of background and foreground browser activity -- over 100 URLs, mostly called from ad-host Yieldmanager by an automated script hosted elsewhere, were pulled down in just the first three seconds after the page loaded," says Webroot's Andrew Brandt.
 At least one site was found to be installing a virus that effectively locks down your PC, terminating most any application before Windows is able to open it. Programs installing spyware and even the Koobface virus have also been observed.
At least one site was found to be installing a virus that effectively locks down your PC, terminating most any application before Windows is able to open it. Programs installing spyware and even the Koobface virus have also been observed.
Staying Safe
The notion of exploiting high-profile news events for spreading spam and malware is nothing new. Security researchers say anytime the public's attention is tuned in to a particular topic, attackers see the potential to move in.
The best line of defense is simply to follow standard Web safety procedures: Delete suspicious-looking e-mails or messages from people whom you don't know; avoid clicking on links in messages if you aren't absolutely sure where they lead; and restrict your surfing to reputable Web sites when it comes to breaking news.
If you use Firefox, you can also install a plugin called NoScript. NoScript blocks JavaScript and Java code from running on any unapproved sites. That could keep you safe from some of the threats lurking behind legit-looking pages.
Thanks for reading, Have a nice day :)!!! Suscribe my post
Tidak ada komentar:
Posting Komentar